Last updated on 8. November 2021
When migrating from Active Directory to the Kerberos SSO extension, we no longer have a dynamic dns update on the client side. It was always a very convenient matter to access the units by their asset name. For example, remote support via ssh or remote desktop. The diversions of the IP address via the client management system seemed too complicated to me.Since there is no dynamic update in the current implementation of the Kerberos SSO extension, I looked for alternatives.
My goal was to have the client update a DNS A entry when it is on the corporate network or VPN.
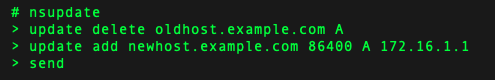
macOS already provides the technical prerequisites by default. In principle, we only need one tool for our project. /usr/bin/nsupdate
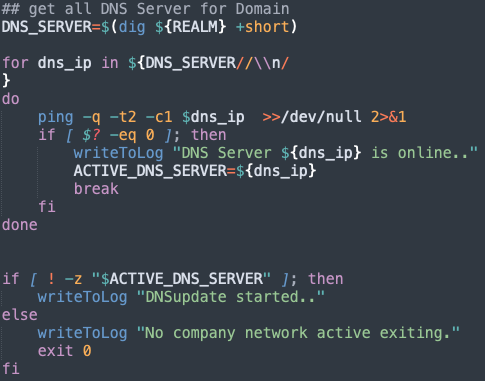
First of all, I had to check whether the device was in the company network. At first I thought that it was enough to ping the domain. I soon realised that I would have problems if one of the DNS servers from my domain was not accessible. Therefore, I now check in the first step whether the returned server is reachable.
Another problem was the fact that the Kerberos ticket had expired or was invalid. To renew the Kerberos ticket, I use the implementation of Kerberos SSO.app-sso --authenticate $REALM
At this point I already knew that the client is in the company network and if it is logged out in the Kerberos SSO extension, it is forced to log in at this point.
This gives me an added value because I can ensure that the local password is synchronised with the directory.
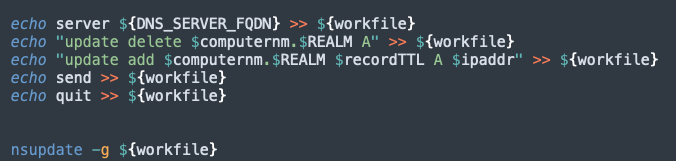
Since it can happen in VPN that the client has several IP addresses, we check on which interface our DNS server can be reached. From this interface we now retrieve the IP address using ipconfig.
ipaddr=`/sbin/ifconfig $Interface | awk '/inet / {print$2}'`To prepare our DNS entry we only need the hostname, which I retrieve using scutil --get ComputerName.
Finally, we create a file with the necessary instructions for the nsupdate tool.
To ensure that our service always starts when there are changes to the network, I have a LaunchAgent that monitors the following files for changes. /etc/resolv.conf/var/run/resolv.conf
We need a LaunchAgent because we use the Kerberos ticket of the user.
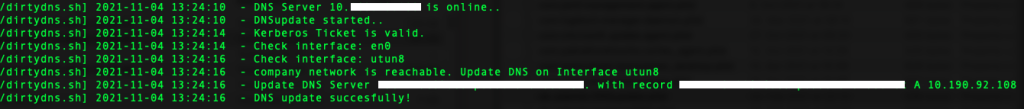
If all requirements are met, our log will show a successful dns update.
I have packaged the script and my LaunchAgent and load the LaunchAgent in the postinstall script.
You can find the necessary files for this project in github.
Since this solution is not really the best, I would appreciate any feedback or suggestions.
Disclaimer
The published information has been carefully compiled, but does not claim to be up-to-date, complete or correct. No liability is assumed for damages resulting from the use of this script or the information drawn from it. This also applies to third-party content accessible via this offer.
Comments